Are you worried about your online security? Do you want to protect your business from cyber-attacks and data breaches? If yes, then a network security engineer is the one you need. They are the professionals who work tirelessly to keep you safe from digital threats.
A network security engineer plays a vital role in ensuring the security of an organization's networks, data and systems. They are responsible for implementing security protocols and technologies, performing security audits, analyzing system vulnerabilities, and developing contingency plans to mitigate threats.
Their job requires them to stay updated with the latest security trends and technological advancements, so that they can provide the most effective security solutions. They work closely with other IT professionals including network administrators, software developers, and business analysts to create a comprehensive security plan.
A network security engineer must have a deep knowledge of various security tools such as firewalls, intrusion detection/prevention systems, and encryption protocols. They must also have excellent analytical and problem-solving skills to assess the potential risks and vulnerabilities of a network.
If you are looking for a career path that will challenge and excite you, then network security engineering is a great choice. As a network security engineer, you will be protecting organizations from cyber-attacks and keeping their information safe. Additionally, this field offers high job security and excellent salary packages.
In conclusion, a network security engineer is a valuable asset for any organization that deals with sensitive information. They are the ones who can ensure that your business remains secure and protected from digital threats. So, invest in a network security engineer today and keep your business secure from any digital danger.
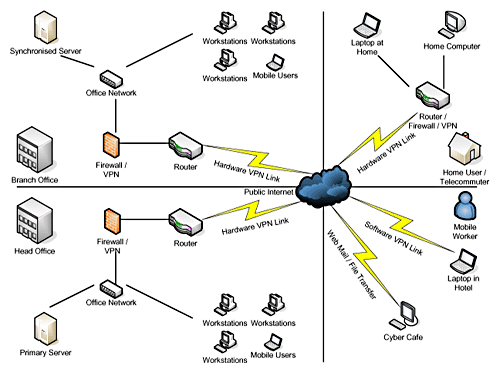
Internet connection
Internet Connection
Congratulations! You’ve made it to the internet, the place where you can access all the knowledge in the world, watch cat videos, and argue with strangers about politics. But, before you dive in, you need to make sure that you have a solid internet connection. Nothing is more frustrating than slow internet or no internet at all.
First things first, you need to have an internet service provider. This can come in the form of a cable company, a telephone company, or a fiber optic company. They will provide the hardware necessary for an internet connection, including a modem and a router. This device will transform a signal from your ISP into a Wi-Fi signal that your device can read.
Now, let’s talk speed. Internet speed is measured in megabits per second (Mbps). The higher the number, the faster your internet connection is. If you plan on streaming movies or playing online games, you’ll need a fast connection. However, if you just need to check emails, a slower connection should suffice.
Next, check your hardware. The older your devices, the slower your internet will be. If you’ve had the same computer for a decade, it’s time for an upgrade. You can also update your Wi-Fi router’s firmware or move it to a different location for better coverage.
Lastly, make sure that you have a secure connection. Password protect your Wi-Fi, so that no one else can hog your connection or access your personal information.
Overall, a solid internet connection is essential to navigating the web. So, make sure that you’re set up for browsing success!