Network security is of paramount importance in today's digital era. In today's world where anything and everything is connected online, threats to network security abound. Cyber-attacks, malware, phishing, and hacking can cause irreparable damage to businesses, institutions, and individuals alike. However, with the proper implementation of network security protocols, organizations can effectively safeguard their systems and data from potential threats.
What is network security?
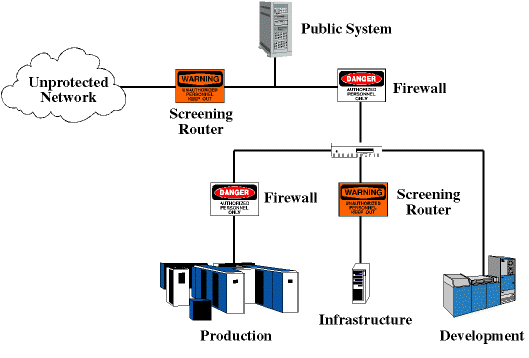
Network security refers to the practice of securing a computer network against unauthorized access or misuse. This can involve implementing software and hardware solutions such as firewalls, antivirus software, VPNs, and Intrusion Detection Systems (IDS) among others.
Why is network security important?
Network security is vital because it helps protect sensitive data such as private information, confidential communications, financial transactions, and intellectual property from being compromised. It also ensures business continuity by preventing network downtime which can cause significant financial losses and damage to the reputation of the organization.
Benefits of network security
- Protection against cyber threats such as malware, ransomware, and phishing attacks
- Improved regulatory compliance
- Enhanced productivity and efficiency by ensuring network uptime
- Safeguarding sensitive data and assets from theft or loss
- Mitigating financial losses and reputational damage from data breaches or system failures
With the increasing dependence on technology and the Internet, network security has become a critical aspect of organizational security. By implementing robust and effective network security protocols, businesses and institutions can ensure the confidentiality, integrity, and availability of their data and assets.